Introduction
These settings directly impact the user journey during sign-up and login and define what screens the user is going to see. The following settings can be adapted in the Developer Panel in the Settings > User interface page:- Sign-up settings: Settings associated with the sign-up part of your user flow
- Login identifiers and fallbacks: Configure the required user information for sign-up and login, as well as the authentication fallback options.
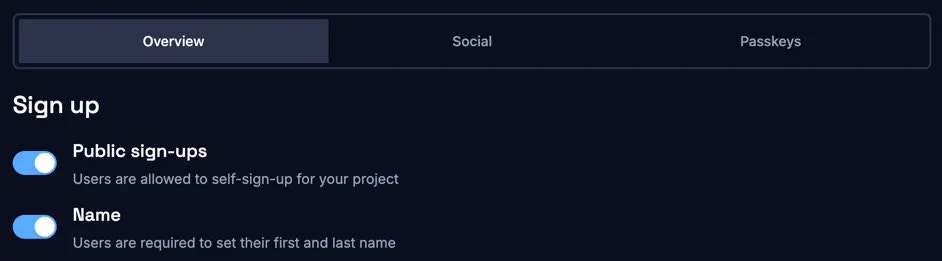
1. Sign-up settings
This section allows you to adjust the sign-up settings. You can configure two settings:- Allow users to self-sign-up for your project.
- Require users to provide their name during sign-up.
2. Login identifiers and fallbacks
Corbado’s UI components support multiple login identifiers. Currently the following login identifier are supported:- Email address
- Phone number
- Username
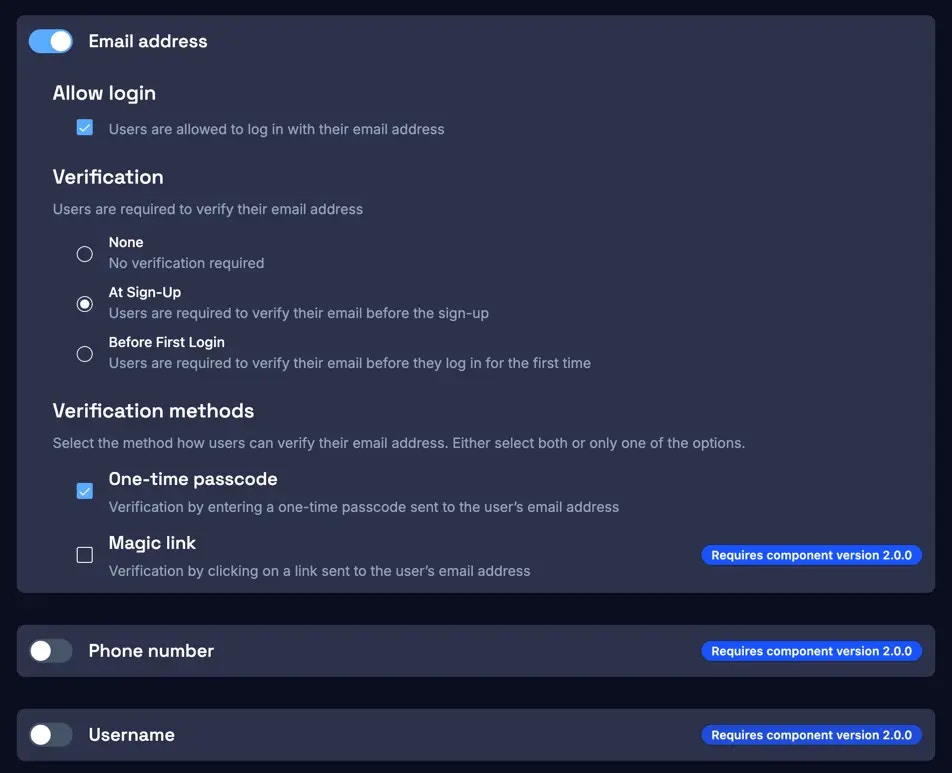
- Verifiable by one-time passcodes or email magic links (email address and phone number)
- Not verifiable (username)
| Login identifier | Allow login | Fallback | Verification stage | Verification methods |
|---|---|---|---|---|
| Email address | Yes | Yes | • None • At sign-up • Before first login | • One-time passcode • Email magic link |
| Phone number | Yes | Yes | • None • At sign-up • Before first login | • One-time passcode |
| Username | Yes | No * | • None | • None |
3.1 Allow login
For each activated login identifier, an additional setting can be adjusted to determine whether it’s allowed for login. If this setting isn’t enabled, the activated login identifier serves after successful sign-up only as a fallback option.
3.2 Fallback
To ensure a smooth sign-up and login process, even when no passkeys are supported or available, a fallback option is offered. If a verifiable login identifier is activated, it automatically serves as the fallback option.Enabling only the username as login identifier will provide no fallback option and may leave users unable to recover accounts or authenticate on devices that do not support passkeys. To address this, it’s recommended to activate a secondary login identifier, without allowing login, to serve as a fallback.
3.3 Verification stage
Define the stage at which your users need to verify their login identifier (email address or phone number). You can select only one option at a time.| Setting | Description |
|---|---|
| None | Users do not have to verify their login identifier. They just sign up by creating a passkey and can immediately log in. |
| Verification before first login (default) | Users that sign up with a passkey are logged in after sign-up. They need to verify their login identifier on their first login though. |
| Verification at sign-up | Users can only create a passkey after verifying their login identifier first. |
3.4 Verification methods
Corbado supports the following two types of verification methods.-
One-time passcode
The one-time passcode (OTP) method entails sending a unique, time-sensitive 6-digit code to the user’s registered email address or phone number. Once received, the user manually inputs this code into the login interface. Upon successful verification, the user gains access to the app or website.
In case you use phone numbers as a login identifier:Corbado offers 10 free SMS per account for testing purposes in development projects. To upper the limit or to integrate SMS verification in a production project, please contact us.
- Email magic link This method involves sending a unique, time-sensitive link to the user’s registered email address. Upon clicking the link, the user is directed to a secure webpage where their identity is confirmed, granting access to the desired app or website. Currently, email magic links are only supported for email address login identifiers.