1. Introduction
Corbado Connect provides native SDKs for both iOS and Android that simplify the integration of passkey authentication into your native apps. By using our SDKs, you can offer a seamless and secure user experience with passkeys, without needing to replace your existing Identity Provider (IdP). The SDKs handle the complexities of the WebAuthn standard and our backend APIs, allowing you to focus on your app’s core functionality. This guide provides a step-by-step approach to integrating the Corbado iOS SDK and Corbado Android SDK. You’ll learn how to implement passkey enrollment, login, and management within your app. For a comprehensive, working example, please refer to our example apps available on GitHub. They are an excellent resource to observe the SDKs in action and to use as a reference during your own implementation. Please note that the example apps use Cognito as an Identity Provider, but the implementation is similar for any other IdP.iOS example App
See the Corbado iOS SDK in action.
Android example App
See the Corbado Android SDK in action.
2. SDK Installation
For the most up-to-date instructions on requirements, installation, and initialization, please refer to the officialREADME in our GitHub repositories. The README provides a comprehensive guide to getting the SDK set up in your project.
Corbado iOS SDK
Learn how to install the Corbado iOS SDK.
Corbado Android SDK
Learn how to install the Corbado Android SDK.
3. Backend Integration
The backend logic required to support Corbado Connect is consistent across all client platforms, whether it’s a web application or an native/mobile application. To maintain a single source of truth and avoid duplicating instructions, we’ve consolidated all backend-related steps into a dedicated guide. Please refer to it for a complete walkthrough of the required session management and API endpoints in your backend:Backend Setup
Learn how to implement the necessary session management and API endpoints in your backend.
getConnectToken(), you must provide the user’s access token to enable the backend to verify their authenticated state.
For more details on access tokens, please refer to the session management section in the Backend Setup guide.
4. Passkey Enrollment
In a typical integration scenario, the initial user sign-up is handled through your existing authentication system’s standard registration process. This could be through:- Email and password registration
- Social login providers
- Enterprise SSO
- Maintains compatibility with your existing user registration flow
- Allows for gradual adoption of passkeys
- Preserves existing user data and relationships
- Enables a smooth transition for your users
4.1 Implementation Overview
The user sign-up and passkey append process consists of a series of coordinated interactions between your mobile native app and backend, your authentication system, and Corbado’s APIs. Here’s a high-level overview of the flow: In the following sections, we will explain each step in detail.4.2 App Integration
Integrating passkey enrollment into your app involves presenting a new screen that encourages authenticated users to create a passkey for future passwordless logins.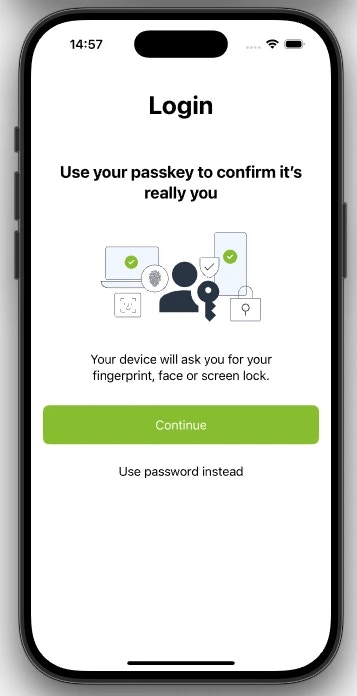
4.2.1 Before Rendering
Before rendering the passkey enrollment screen, you should call theisAppendAllowed() method from the Corbado iOS/Android SDK. This function is crucial for determining if the current user is eligible to add a passkey, based on your configurations for Gradual Rollout and Passkey Intelligence.
The method requires a connectTokenProvider, a closure that fetches a connect token from your backend. We’ll use the AppBackend helper class defined previously. You need to provide the user’s current access token so your backend can verify their authenticated state before generating the token.
4.2.2 On Button Click
When the user taps the button to create a passkey, you must call thecompleteAppend() method from the Corbado iOS/Android SDK. This function initiates the native passkey creation ceremony, which securely interacts with the device’s hardware and Corbado’s backend.
The method returns a status indicating the outcome of the ceremony, which you should handle accordingly.
5. Passkey Login
Now that users can append passkeys to their accounts, we can enable a truly passwordless login experience. The goal is to authenticate a user with their passkey using Corbado Connect and, upon successful verification, obtain a new access token from your system. The complete flow is illustrated in detail in our User Login Flow documentation.5.1 Implementation Overview
The user login process consists of a series of coordinated interactions between your mobile native app and backend, your authentication system, and Corbado’s APIs. Here’s a high-level overview of the flow: In the following sections, we will explain each step in detail.5.2 App Integration
Integrating passkey login into your app is slightly more complex than passkey enrollment because it requires direct integration with your existing login screen and involves handling several different cases and potential UI states across multiple screens.5.2.1 Before Rendering
Before rendering the login screen, you should call theisLoginAllowed() method from the Corbado iOS/Android SDK. This function is crucial for determining if the current user is eligible to use a passkey, based on your configurations for Gradual Rollout and Passkey Intelligence.
5.2.2 Overlay Login
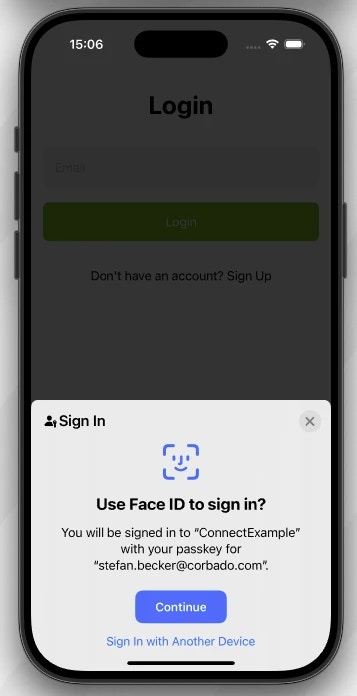
loginWithoutIdentifier() method from the Corbado iOS/Android SDK.
If the login has been successful (.done / .Done), you must verify the returned signedPasskeyData with your backend using the helper method completeLogin() implemented earlier.
5.2.3 Textfield Login
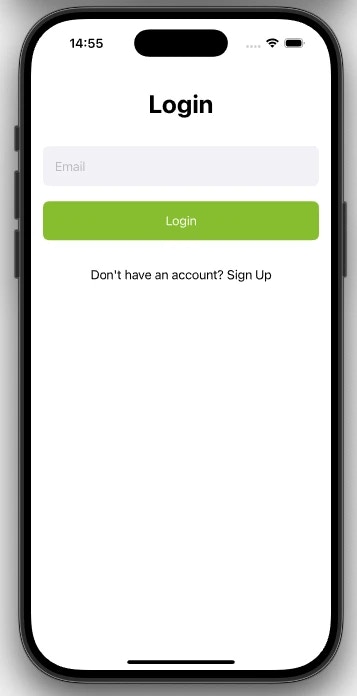
loginWithIdentifier() method from the Corbado iOS/Android SDK.
Just like with other flows, a successful login returns .done / .Done with signedPasskeyData, which you must verify with your backend.
5.2.4 One-Tap Login
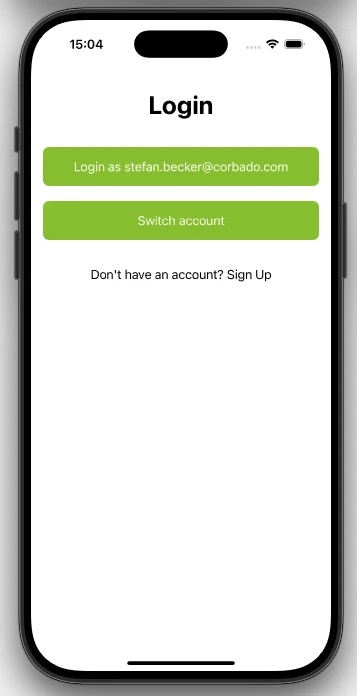
loginWithOneTap().
The subsequent steps for handling the response are identical to the Textfield Login flow: you will need to handle the different cases returned by the method and ultimately verify the signedPasskeyData with your backend.
5.2.5 Fallback Login
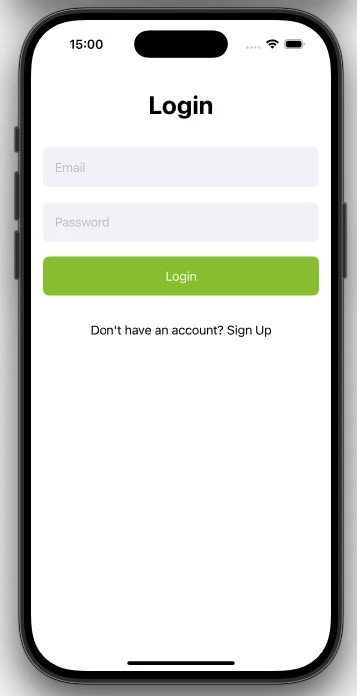
6. Passkey Management
Providing users with a way to manage their passkeys is a critical part of the experience. Your application should offer a secure, authenticated area (like a profile or settings page) where users can list, delete, and add new passkeys. The Corbado iOS/Android SDK provides all the necessary methods to build this functionality into your app. The complete passkey management flow is also illustrated in detail in our Passkey Management Flow documentation.6.1 Implementation Overview
The passkey management process consists of a series of coordinated interactions between your mobile native app, your backend, and Corbado’s APIs. Here’s a high-level overview of the flow for listing passkeys. The flows for deleting and creating a new passkey are similar. In the following sections, we will explain each step in detail.6.2 App Integration
All passkey management operations are security-sensitive and must be authorized. For this purpose, the Corbado iOS/Android SDK uses a connect token that you generate on your backend for an authenticated user. To provide this token to the Corbado iOS/Android SDK in a secure and timely manner, all management methods require aconnectTokenProvider. This is a closure that the SDK calls just before executing an operation to get a fresh connect token. You can reuse the AppBackend helper class for this.
6.2.1 List Passkeys
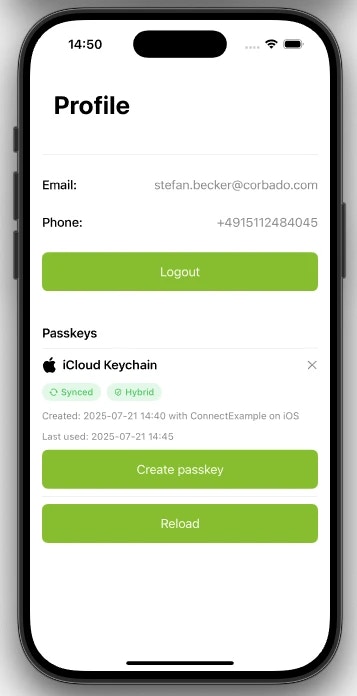
isManageAppendAllowed() method from the Corbado iOS/Android SDK conveniently provides both pieces of information in a single call.
This eligibility check is governed by your project’s settings for Gradual Rollout and Passkey Intelligence. The method returns the list of existing passkeys along with a status indicating if the “Add new passkey” button should be displayed.
6.2.2 Delete Passkey
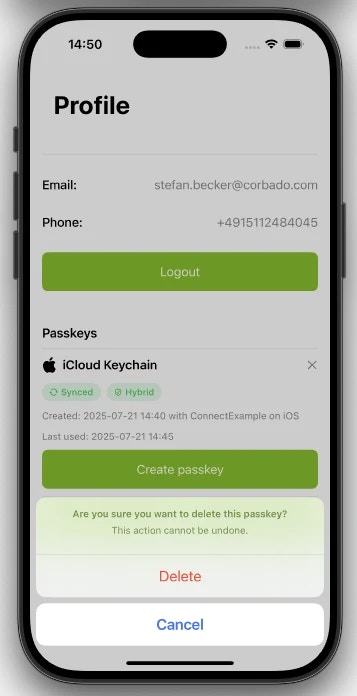
deletePasskey() method from the Corbado iOS/Android SDK.
This operation also requires authorization, so you must provide the same connectTokenProvider as before to generate a fresh connect token of type PasskeyDelete.
6.2.3 Create Passkey
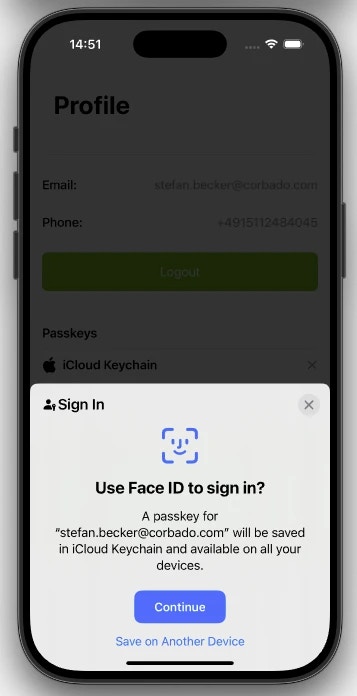
isManageAppendAllowed() method), your UI should present an “Add new passkey” button. When the user taps this button, you call the completePasskeyListAppend() method from the Corbado iOS/Android SDK.
This function initiates the native passkey creation ceremony. It requires a connectTokenProvider to authorize the action, but for this operation, you must request a connect token of type PasskeyAppend from your backend.