1. Executive Overview
In today’s regulatory landscape, financial institutions, payment service providers, government entities, and other regulated organizations require absolute control over their authentication infrastructure and data. Corbado Connect’s Enterprise Passkey Export capability, available exclusively with Enterprise Private Cloud deployments, directly addresses critical requirements for vendor independence, regulatory compliance, and operational resilience mandated by frameworks such as the European Banking Authority (EBA) guidelines, North American outsourcing regulations (OCC, OSFI), and national payment network regulations. This Private Cloud feature leverages your single-tenant infrastructure to ensure complete sovereignty over authentication data while utilizing Corbado’s advanced passkey capabilities. By providing automated, secure, and fully portable authentication data exports, we eliminate vendor lock-in concerns and enable comprehensive business continuity planning, which are essential requirements for regulated entities operating in critical infrastructure sectors.1.1 Private Cloud Enterprise Capabilities
- Automated Daily Data Archival: Production-grade automated export processes execute daily, creating immutable authentication data archives in industry-standard formats
- Enterprise-Grade Security Architecture: All exports are secured using AWS S3’s enterprise security features, including encryption at rest (AES-256) and in transit (TLS 1.3)
- Management Console Integration: Executive dashboards and administrative interfaces provide controlled access to historical authentication data exports
- Complete Data Portability: Full WebAuthn credential export enables seamless migration to alternative authentication providers or in-house systems
- Vendor Independence Assurance: Comprehensive data export capabilities ensure your organization retains the ability to transition authentication providers without service disruption
1.2 Strategic Business Applications
The Enterprise Passkey Export capability addresses critical requirements across regulated industries:- Regulatory Audit Readiness: Maintain comprehensive authentication data archives to satisfy regulatory examination requirements from banking supervisors, financial regulators, and compliance auditors
- Vendor Substitution Rights: Exercise contractual rights for vendor replacement without data loss, ensuring compliance with procurement regulations and vendor risk management policies
- National Payment Network Resilience: Meet national infrastructure requirements for payment service providers, including data localization, sovereignty, and disaster recovery mandates
- Business Continuity Planning: Implement vendor-independent authentication data backup strategies beyond Corbado’s existing disaster recovery infrastructure, enabling restoration without vendor support in extreme scenarios while maintaining alignment with Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO)
- Multi-Jurisdictional Compliance: Address data residency requirements, cross-border data transfer regulations, and jurisdiction-specific authentication data retention policies
- Exit Strategy Implementation: Execute pre-defined vendor transition plans with zero authentication data loss, maintaining service continuity during provider changes
- Operational Risk Management: Mitigate single points of failure in authentication infrastructure through comprehensive data export and portability capabilities
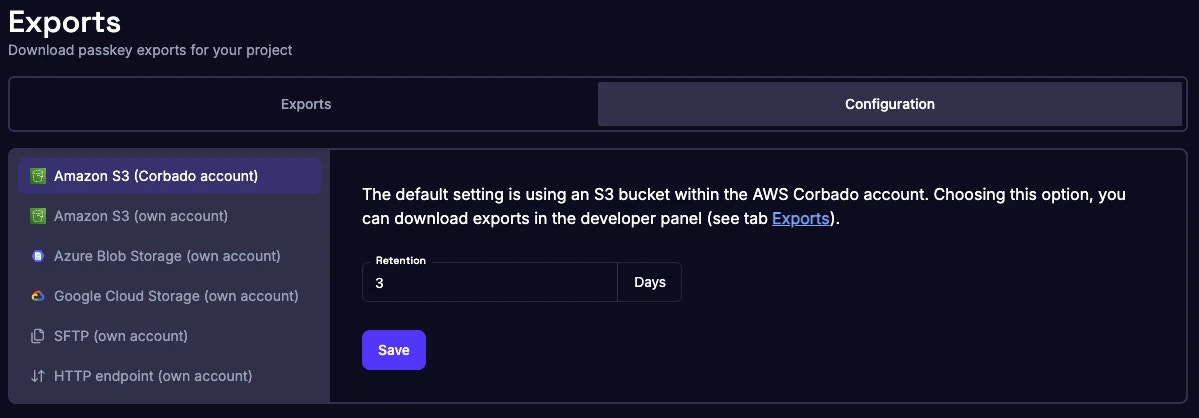
1.3 Storage Architecture Options
Enterprise Private Cloud deployments provide multiple storage models to align with your organization’s data governance, compliance requirements, and operational preferences:1.3.1 Standard Private Cloud: Corbado-Managed Dedicated Storage
The standard Enterprise Private Cloud implementation provides each customer with a dedicated S3 bucket within their single-tenant isolated Corbado environment. This approach delivers enterprise-grade security while minimizing operational overhead for your teams. Key Features:- Dedicated Storage: Your passkey exports are stored in an S3 bucket exclusively allocated to your organization within your dedicated Corbado installation
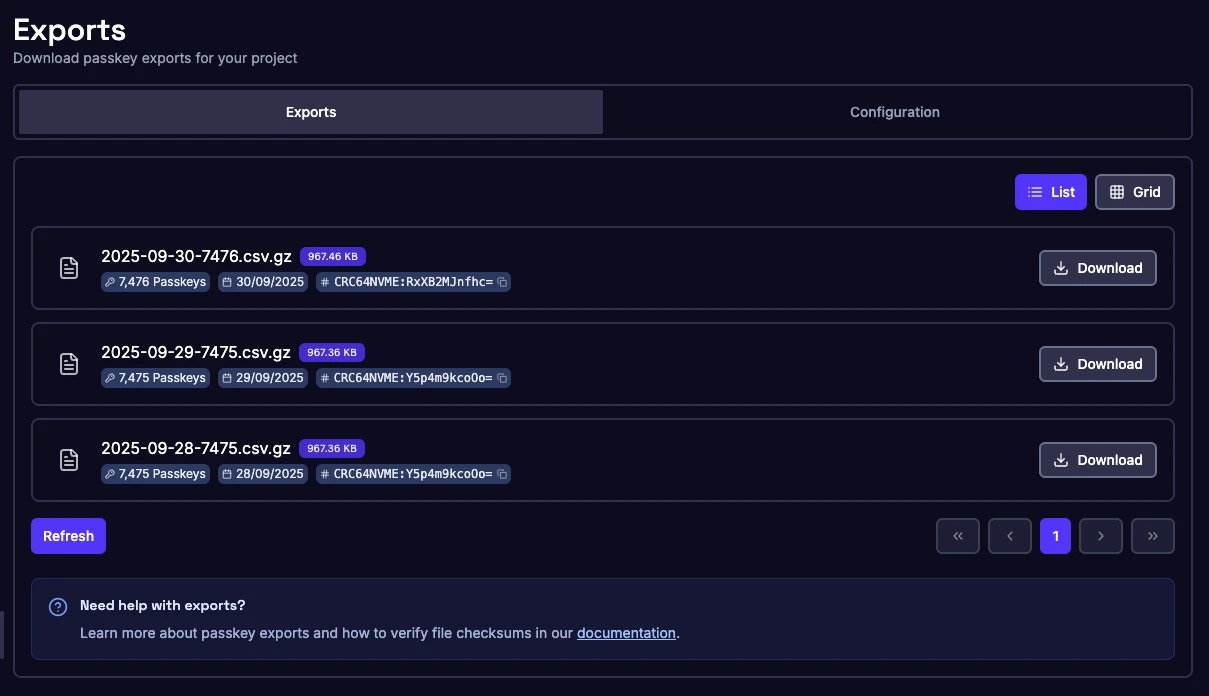
- Management Console Access: Download URLs for exported files are readily available through the Corbado Management Console
- Manual Download Capability: Authorized administrators can initiate downloads on-demand for compliance audits, migrations, or backup purposes
- Secure Access: All downloads require authentication through the Management Console with role-based access controls
- Data Retention: Standard 3-day retention with automated cleanup, configurable based on your requirements
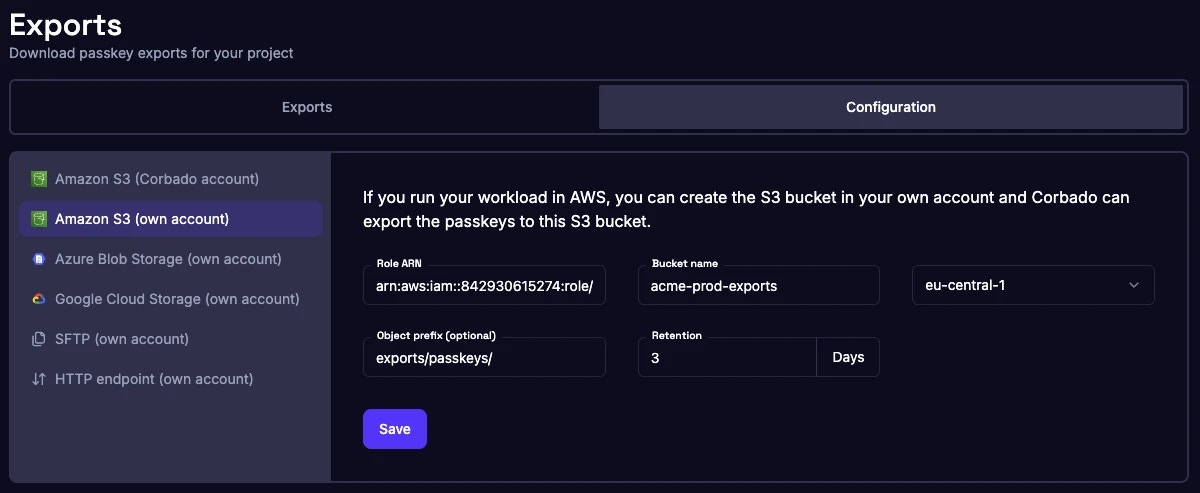
1.3.2 Advanced Private Cloud: Customer-Controlled Storage Infrastructure
For Private Cloud customers with specific data sovereignty or compliance requirements, passkey exports can be configured to deliver directly to your own AWS S3 storage infrastructure. This approach ensures authentication data resides entirely within your organization’s control while maintaining automated export delivery from your dedicated single-tenant Corbado environment. Security and Compliance Architecture:- Secure Access Control: Corbado accesses your storage using temporary, limited-scope credentials that you control and can revoke at any time
- Data Ownership: All exported data is immediately owned by your organization upon delivery, with no retained access by Corbado
- Encryption at Rest: Supports your organization’s encryption keys, ensuring only you can decrypt the exported authentication data
- Audit Trail: All data transfers are logged and traceable for compliance reporting and security audits
- Tenant Isolation: Each customer’s exports are cryptographically isolated using unique identifiers to prevent any cross-tenant data access
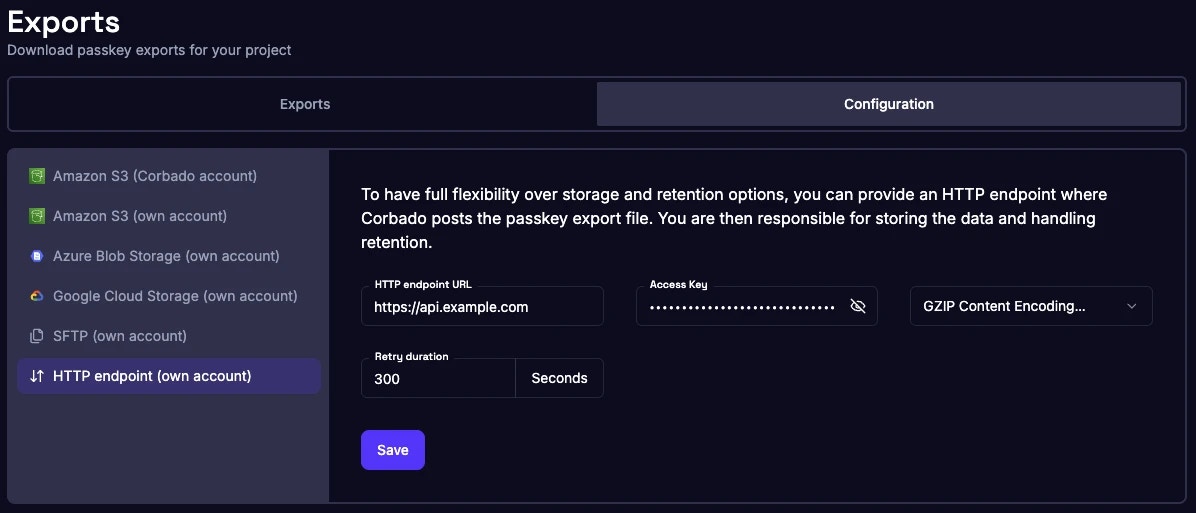
1.3.3 Private Cloud Enterprise Plus Addon: Custom Storage Solutions
For Private Cloud customers with the Enterprise Plus addon, Corbado enables additional storage customization options beyond standard cross-account S3 configurations:- Alternative Cloud Providers: Integration with Azure Blob Storage, Google Cloud Storage, or other enterprise storage platforms
- On-Premises Delivery: Direct delivery to on-premises storage systems via secure channels (SFTP, AWS Storage Gateway, or dedicated connectivity)
- Geographic Data Residency: Region-specific storage with configurable data sovereignty controls
- Custom Retention Policies: Automated lifecycle management aligned with your organization’s data retention requirements
- Multi-Region Replication: Automated replication to multiple storage locations for enhanced disaster recovery
2. Technical Specifications: Export Data Schema
2.1 Data Format and Compliance Standards
Corbado Connect delivers authentication data exports in a standardized CSV format, ensuring compatibility with enterprise data management systems, compliance reporting tools, and authentication infrastructure platforms. This format has been specifically designed to meet audit trail requirements, facilitate vendor transitions, and support comprehensive disaster recovery scenarios. Each exported file contains a complete snapshot of your organization’s passkey credentials, with every row representing a unique WebAuthn credential including all cryptographic material and metadata required for authentication system portability. The export format adheres to industry standards including:- W3C WebAuthn Specification compliance for credential data representation
- RFC 4648 Section 5 encoding standards for cryptographic materials
- ISO 8601 timestamp formatting for audit trail compatibility
- CSV RFC 4180 formatting for maximum interoperability
2.2 Authentication Data Field Specifications
The following table provides comprehensive documentation of each data field included in the export, essential for your technical teams, compliance officers, and audit personnel:| Field | Description | Data Type & Encoding | Compliance & Audit Relevance |
|---|---|---|---|
userId | Corbado-assigned unique user identifier | String (UUID v4) | Internal audit trail correlation |
externalUserId | Organization-specific user identifier | String | Primary key for enterprise identity systems integration |
credentialId | WebAuthn credential identifier | Base64URL with padding (RFC 4648 §5) | Unique credential tracking for compliance reporting |
publicKey | COSE-encoded public key for credential verification | Base64URL with padding (RFC 4648 §5) | Cryptographic material for authentication validation |
authenticatorSignCount | Signature counter for replay protection | Integer (32-bit unsigned) | Security audit and anomaly detection |
authenticatorAaguid | Authenticator Attestation GUID | UUID format (RFC 4122) | Device identification for risk assessment |
authenticatorAttachment | Platform vs. cross-platform indicator | Enum: platform | cross-platform | Device binding compliance verification |
backupEligible | Cloud backup capability indicator | Boolean | Disaster recovery planning metric |
backupState | Current backup synchronization status | Boolean | Business continuity assessment |
transports | Supported authentication transport protocols | Semicolon-delimited (e.g., usb;nfc;ble;internal) | Multi-factor authentication compliance |
attestationFormat | WebAuthn attestation statement format | String (e.g., packed, fido-u2f, none) | Authenticator trust evaluation |
created | Credential registration timestamp | ISO 8601 (e.g., 2024-01-15T10:30:00.000Z) | Audit trail and retention policy enforcement |
status | Credential lifecycle status | Enum: active | suspended | revoked | Access control and compliance state |
All cryptographic materials are exported in their complete form, ensuring zero data loss during vendor transitions. The Base64URL encoding with padding ensures compatibility with all major authentication frameworks and maintains the integrity of cryptographic signatures required for WebAuthn authentication flows.
3. Enterprise Integration and Migration Pathways
3.1 Vendor Transition and Business Continuity Implementation
The Enterprise Passkey Export capability has been architected to support seamless authentication provider transitions, ensuring zero disruption to your organization’s authentication services during vendor migration scenarios. Whether executing a planned vendor transition as part of strategic sourcing initiatives or responding to business continuity events, the exported authentication data provides complete portability across authentication platforms. Our export format ensures compatibility with enterprise-grade authentication systems, enabling your organization to:- Execute vendor transitions within defined maintenance windows
- Maintain authentication service availability during provider migrations
- Preserve user authentication history for compliance and audit purposes
- Implement multi-vendor authentication strategies for risk mitigation
3.2 Enterprise Authentication Platform Compatibility
The exported authentication data maintains full compatibility with industry-leading WebAuthn implementations, ensuring seamless integration with your existing or target authentication infrastructure:3.2.1 Enterprise Development Frameworks
- JavaScript/TypeScript: SimpleWebAuthn - Production-ready WebAuthn implementation for Node.js and browser environments
- Python: py_webauthn - Enterprise Python library supporting Django, Flask, and FastAPI integrations
- Go: go-webauthn/webauthn - High-performance implementation for microservices architectures
- Java: webauthn4j, Yubico Java WebAuthn Server - Enterprise Java solutions for Spring Boot and Jakarta EE
- C#/.NET: Fido2NetLib - Microsoft-ecosystem compatible library for .NET Core and Azure deployments
- PHP: lbuchs/WebAuthn - Production-grade PHP implementation for Laravel and Symfony frameworks
3.3 Reference Implementation: Migration Pattern
To demonstrate the practical application of our data portability solution, we provide a reference implementation for importing exported passkey credentials into the industry-standard SimpleWebAuthn library. This implementation illustrates the straightforward nature of credential migration, enabling organizations to rapidly prototype and validate their authentication migration strategies. The following code can be directly integrated into the official SimpleWebAuthn example repository to establish a functional migration pathway.- Credential Filtering: Processes only active credentials to maintain authentication system integrity
- Cryptographic Material Handling: Properly decodes Base64URL-encoded credential IDs and public keys per WebAuthn specifications
- Transport Protocol Parsing: Maintains multi-factor authentication compatibility through transport method preservation
- Idempotent Import Logic: Implements duplicate detection to ensure safe re-execution during migration testing
- Operational Visibility: Provides console output for migration validation and troubleshooting
4. Checksum Verification and Data Integrity
4.1 Enterprise-Grade Data Integrity Controls
Corbado’s Enterprise Passkey Export implements rigorous data integrity controls to ensure the authenticity and completeness of exported authentication data. Each export file is cryptographically verified using industry-standard checksum algorithms, providing your organization with independently verifiable proof that exported data remains unaltered during transmission and storage. The checksum verification system addresses critical requirements for regulated industries:- Regulatory Compliance: Satisfies data integrity requirements for financial services, healthcare, and government sectors
- Audit Trail Validation: Provides cryptographic proof of data integrity for compliance auditors and security teams
- Tamper Detection: Enables immediate identification of any unauthorized modifications to exported authentication data
- Chain of Custody: Establishes verifiable chain of custody for authentication data from export to import
4.2 CRC64NVME Checksum Implementation
To ensure performance at enterprise scale while maintaining cryptographic integrity, Corbado implements theCRC64NVME checksum algorithm for all passkey exports. This algorithm is specifically designed for high-performance verification of large datasets, making it ideal for organizations with substantial user bases requiring millions of passkey credentials.